
This post was co-written by Karen Crumbley and Keith Haskett, Rebyc Security. Karen has been providing Educational Risk Mitigation online training courses and encouraging community bankers to engage in conversations with their peer banks and vendors about how best to mitigate risks within their own institutions. She has also been a valued member of Jack Henry & Associates for thirteen years. Keith led the Risk and Information Security Consulting Services practice at CSI for several years, then co-founded Rebyc to deliver offensive security solutions customized to meet the needs of the highly-regulated, financial services industry.
Despite all of the strides made in the security industry to mitigate phishing scams, they continue to be one of the most successful forms of fraud. One of the primary reasons is due to the extensive efforts bad actors are making to research and observe their targets’ behavior. They monitor and research the users’ activity in order to craft sophisticated and convincing emails that even computer-savvy users struggle to identify, known as spear phishing attacks. Financial institutions (FIs) are faced with combatting phishing fraud through Information Security Awareness and Social Engineering Testing to keep employees up to date on the latest scams. The following list includes common types of spear phishing fraud targeting FI employees. You can share this information across your organization to boost ongoing education efforts.
Spear phishing attacks target senior leaders and executives – Very Attacked People (VAP) – because they have administrative access to valuable non-public information or corporate funds. The image below is an example of this type of spear phishing attack involving Bank Secrecy Act (BSA) officers. The sender of the message appears to be another BSA officer requesting the attached PDF document be opened because it contains details regarding a suspicious transfer. The PDF in fact contains a link to a malicious website where the unsuspecting officer may download malware or compromise their machine, allowing would-be criminals to obtain sensitive information. Note that the image below contains the misspelled word, “suspicions”. Misspelled words are common indicators of a phishing email.
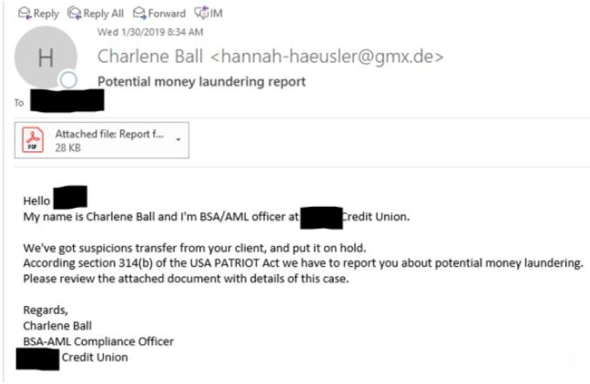
Source: KrebsonSecurity
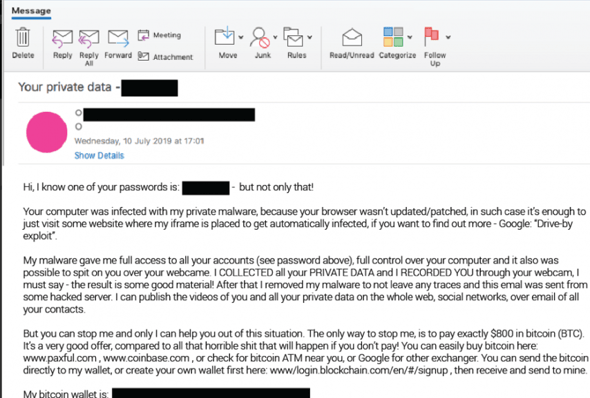
Some attackers attempt to go after their targets by threatening to expose their private, sensitive information. For instance, Cofense Labs recently released a list of over 200 million emails and domains that they believe are part of an extortion campaign. The attacker in the example below attempts to shame the victim into providing bitcoin in order to keep their information from being exposed.
Romance fraud uses mobile app dating sites such as Tinder, Bumble, or Match.com to phish victims. The bad actors use fake identities to build a relationship online with their victims, and eventually they begin to request access to funds or private information. Often claiming to be in the military or traveling overseas, they ask their victim to wire money to buy a flight, send a gift card to help with medical expenses, or claim some other hardship while playing on the emotions of their new connection. According to the 2018 FBI Internet Crime Report, there were over 18,000 cases of romance fraud during the year, resulting in over $362 million in losses. Those numbers represent a 20% increase in cases and more than a 70% increase in losses compared to the previous year.
A typical Business Email Compromise (BEC) phishing example begins with a fraudster spoofing an email from an executive at a company, attempting to get an authorized employee to generate a wire. The bad actor achieves this through observing how the executive interacts with staff, the language they use for requests, and what tone they use in their communications. For example, the impersonator requesting a wire transfer may ask the victim about personal information, such as how their son is doing after knee surgery, in order to be more convincing. According to a recent Dark Reading article, BEC attacks were up 67% in 2018, and 73% of those attacked experienced losses.
Clearly, your bank or credit union will continue to encounter spear phishing attacks. Recognizing that these attacks will evolve and providing your staff with suspicious email examples will assist in diminishing risks. Taking opportunities to communicate with your employees during staff meetings, sending regular information security email communications, and providing education throughout the year will also keep the topic as a focal point and create a culture of information security awareness.
In summary, the best thing your institution can do to avoid being phished is to be aware and create a plan to limit the damage.
Additional Resources:
Stay up to date with the latest people-inspired innovation at Jack Henry.
.svg)

Learn more about people-inspired innovation at Jack Henry.
Who We Serve
What We Offer
Who We Are