
File Integrity Monitoring is a technology that monitors and detects changes in files that may indicate a cyberattack. Unfortunately, for many banks and credit unions, File Integrity Monitoring mostly means noise: too many changes, not enough context around these changes, and very little insight into whether a change actually poses a risk. File Integrity Monitoring is a critical security control, but it must provide sufficient insight and actionable intelligence.
File Integrity Monitoring exists because change is prolific in IT environments. Hardware assets change. Software programs change. Configuration states change. Some of these modifications are authorized insofar as they occur during a patch cycle – some cause concern by their unexpected nature.
Otherwise known as change monitoring, file integrity monitoring involves examining files and folders to see if and when they change, how they change, who changed them, and what can be done to restore those files if those modifications are unauthorized. As such, file integrity monitoring is useful for detecting malware as well as achieving compliance.
Today, malicious actors or insiders can cause mayhem inside your networks, changing configuration files, critical system or application files, or data … and then delete event logs to hide their tracks.
Knowing who’s accessing critical files and when changes occur to them is required by regulatory standards and laws. It is necessary to protect your organization’s critical assets and data and detect a breach. Fortunately, meeting these regulatory requirements with a SIEM solution is easy. File Integrity Monitoring automatically identifies anomalous file changes across your environment and notifies you when suspicious activity takes place on critical files, so you can take action and prove compliance.
Set a policy: FIM begins when your organization defines a relevant policy. This step involves identifying which files on which computers the company needs to monitor.
Establish a baseline for files: Before we can actively monitor files for changes, organizations need a reference point against which they can detect alterations. Therefore, we need to document a baseline, or a known good state for files that will fall under their file integrity monitoring policy. This standard should take into account the version, creation date, modification date, and other data that can help IT professionals provide assurance that the file is legitimate.
Monitor changes: With a detailed baseline, organizations can proceed to monitor all designated files for changes. They can augment their monitoring processes by auto-promoting expected changes, thereby minimizing false positives.
Send an alert: If the file integrity monitoring solution detects an unauthorized change, those responsible for the process should send out an alert to the relevant personnel who can fix the issue.
Report results: FIM tools are often used for ensuring regulatory compliance. In that event, your organization can generate reports for audits in order to substantiate the deployment of their file integrity monitoring assessor.
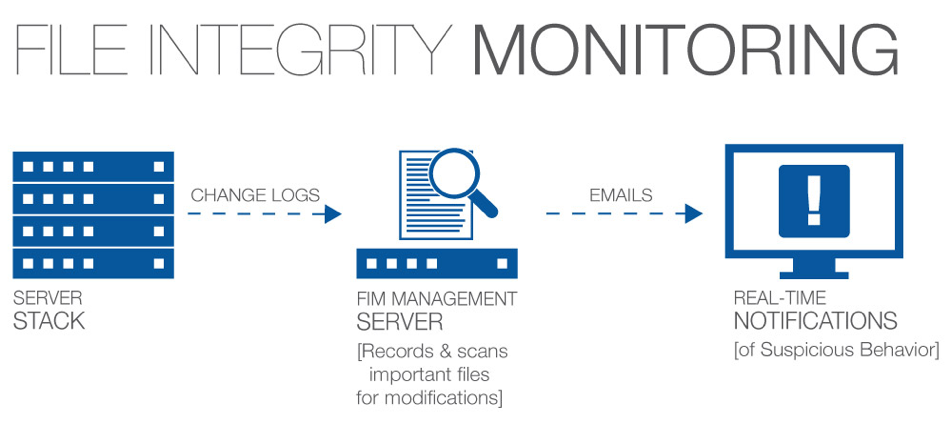
Every security breach begins with a single change. A small alteration to one file can expose your whole network to a potential attack. File integrity monitoring, in its simplest sense, is about keeping track of change from an established baseline and alerting you to any unexpected change that may represent a security risk or a compromise in regulatory compliance. Whether it’s a phishing scam, DDoS attack, malware, ransomware, or insider threat, your File Integrity Monitoring solution should alert you right away anytime a cybercriminal is penetrating your system. file integrity monitoring solutions will capture your system’s configuration baseline and deliver the “who, what, and when” details of each relevant file change – without bogging you down in notifications about routine changes.
Stay up to date with the latest people-inspired innovation at Jack Henry.
.svg)

Learn more about people-inspired innovation at Jack Henry.
Who We Serve
What We Offer
Who We Are